Sign Git Commits
Git is a very flexible tool. It allows one to commit using any name they want. So, for example, an attacker could commit a code using the disguised name of another person, and then push it to a repository.
*Main article: *Git: Change Author
So, how would one be sure if the commit is genuine and has a verified author? It's done with signing.
Instructions
A well-established way of signing commits is using GNU Privacy Guard, GPG in short.
Install GNU Privacy Guard, GPG
To be able to sign commits, one needs to install the gpg software first. On Ubuntu:
sudo apt-get install gpa seahorse
On Mac:
brew install gpg
The package is most likely available for the native package manager of other Linux distributions. Bottom line, one could install Homebrew on Linux.
Generate New GPG Key
Now, generate a key:
gpg --gen-key
The software will ask for your name and email address. Please make sure to enter an email address verified on your GitHub account. If you want to keep your email address private, you can use your GitHub no-reply email address.
A prompt will then ask for a passphrase to protect your key. Enter one twice.
Now, take a look at your key:
gpg --list-secret-keys --keyid-format=long
The output should be something like this:
/home/mohammad/.gnupg/pubring.kbx
------------------------------
sec rsa3072/3AA5C34371567BD2 2022-09-15 [SC] [expires: 2024-09-14]
659FF1F3B51AD9F677276E4BC0C2F9C91A262A2D
uid [ultimate] Mohammad-Ali A'râbi <44623032+aerabi@users.noreply.github.com>
ssb rsa3072/42B317FD4BA89E7A 2022-09-15 [E] [expires: 2024-09-14]
Or perhaps something like this:
/Users/mohammad/.gnupg/secring.gpg
------------------------------------
sec 4096R/3AA5C34371567BD2 2016-03-10 [expires: 2017-03-10]
uid Mohammad <me@example.com>
ssb 4096R/42B317FD4BA89E7A 2016-03-10
Either way, the key is the part after the slash and before the date. Copy it, because we will need it later.
First, we need to tell git that we are using this key for signing commits:
git config --global user.signingkey 3AA5C34371567BD2
Second, we need to export the key so that we can give it to GitHub later:
gpg --armor --export 3AA5C34371567BD2
Make sure to replace the key from this command with your own. This command shows you a key beginning with -----BEGIN PGP PUBLIC KEY BLOCK----- and ending with -----END PGP PUBLIC KEY BLOCK-----. Copy it. You can also store it in a file for safekeeping:
gpg --armor --export 3AA5C34371567BD2 > gpg-key.txt
Add GPG Key to GitHub Account
The next step is to save the GPG key in your GitHub account. Go to the keys part in your settings: https://github.com/settings/keys
Click on "New GPG key", paste the key (the one beginning with -----BEGIN PGP PUBLIC KEY BLOCK----- and ending with -----END PGP PUBLIC KEY BLOCK-----) into the big text area, give it a name, and click "Add GPG key".
Create Your First Signed Commit
Do some changes, stage them, and then commit passing -S flag:
git commit -S -m ":pencil: Add alt text for the header images"
The OS asks you for the passphrase you set in the beginning. Enter it. Bingo! 🎉
To check the signatures, use the following command:
git log --show-signature
The output will be something similar to this:
commit 79db00a5d6724ebf304b268bd696c03aafcdd232 (HEAD -> master, origin/master, origin/HEAD)
gpg: Signature made Do 15 Sep 2022 23:18:52 CEST
gpg: using RSA key 659FF133B51AA9F677276E4BC1D2F9C91A262A2D
gpg: Good signature from "Mohammad-Ali A'râbi <me@example.com>" [ultimate]
Author: Mohammad-Ali A'râbi <me@example.com>
Date: Thu Sep 15 23:15:54 2022 +0200
:pencil: Add alt text for the header images
If you push your commit, GitHub will add a "verified" badge to it:
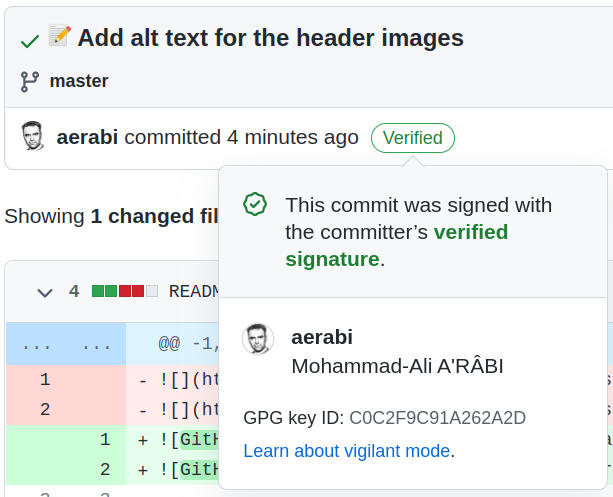
Last Words
To tell git to sign the commits by default (without passing -S), set the following config:
git config --global commit.gpgSign true
To sign a tag, you should pass a small -s:
git tag -s v1.5
And to make it automated for tags:
git config --global tag.gpgSign true
Most IDEs and editors support GPG signing, so you can sign your commits directly from there, and in most cases, you won't need to enter the passphrase every time.
And yes, you can add emojis to your git commit messages. 😅
I write a blog post on git every week.
- Subscribe to my Medium publishes to get notified when a new Git Weekly issue is published.
- Follow me on Twitter for more updates and articles published on other platforms.
References
- Chacon, Scott, and Ben Straub. "7.4 Git Tools --- Signing Your Work". Pro Git.
- GitHub Docs: Adding a GPG key to your GitHub account
- GitHub Docs: Generating a new GPG key
- GitHub Docs: Signing commits
- GitHub Docs: Telling Git about your signing key
- Kumar, Ankur. Github: Signing commits using GPG (Ubuntu/Mac)

